AWS IoT VPN: Your Ultimate Guide To Secure Connectivity
Hey there, tech enthusiasts! If you're diving into the world of IoT and cloud computing, you’ve probably heard the buzz around AWS IoT VPN. But what exactly is it, and why should you care? AWS IoT VPN is more than just a tech term—it’s your gateway to secure, reliable, and scalable communication between devices and the cloud. Whether you’re managing a small smart home setup or running an industrial IoT network, understanding AWS IoT VPN can transform how you approach device connectivity. So, buckle up because we’re about to break it down for you in a way that’s easy to grasp yet packed with actionable insights!
In today’s hyper-connected world, security and efficiency are non-negotiable. That’s where AWS IoT VPN comes into play. This powerful tool ensures your IoT devices can communicate securely with AWS services without compromising performance. From encryption to identity management, AWS IoT VPN offers features that are game-changing for anyone working with IoT ecosystems. Let’s explore why this matters and how it can benefit you.
Now, you might be wondering, “Is AWS IoT VPN worth the hype?” The short answer is yes, but let’s dive deeper to uncover the reasons. Whether you’re a developer, IT admin, or just someone curious about the tech behind IoT, this guide will walk you through everything you need to know. From setting it up to troubleshooting common issues, we’ve got you covered. So, let’s get started!
- Mr Bean Passed Away A Celebration Of A Timeless Comedian
- Cinasworldx The Ultimate Guide To A Digital Phenomenon Taking Over The Web
What Is AWS IoT VPN and Why Should You Care?
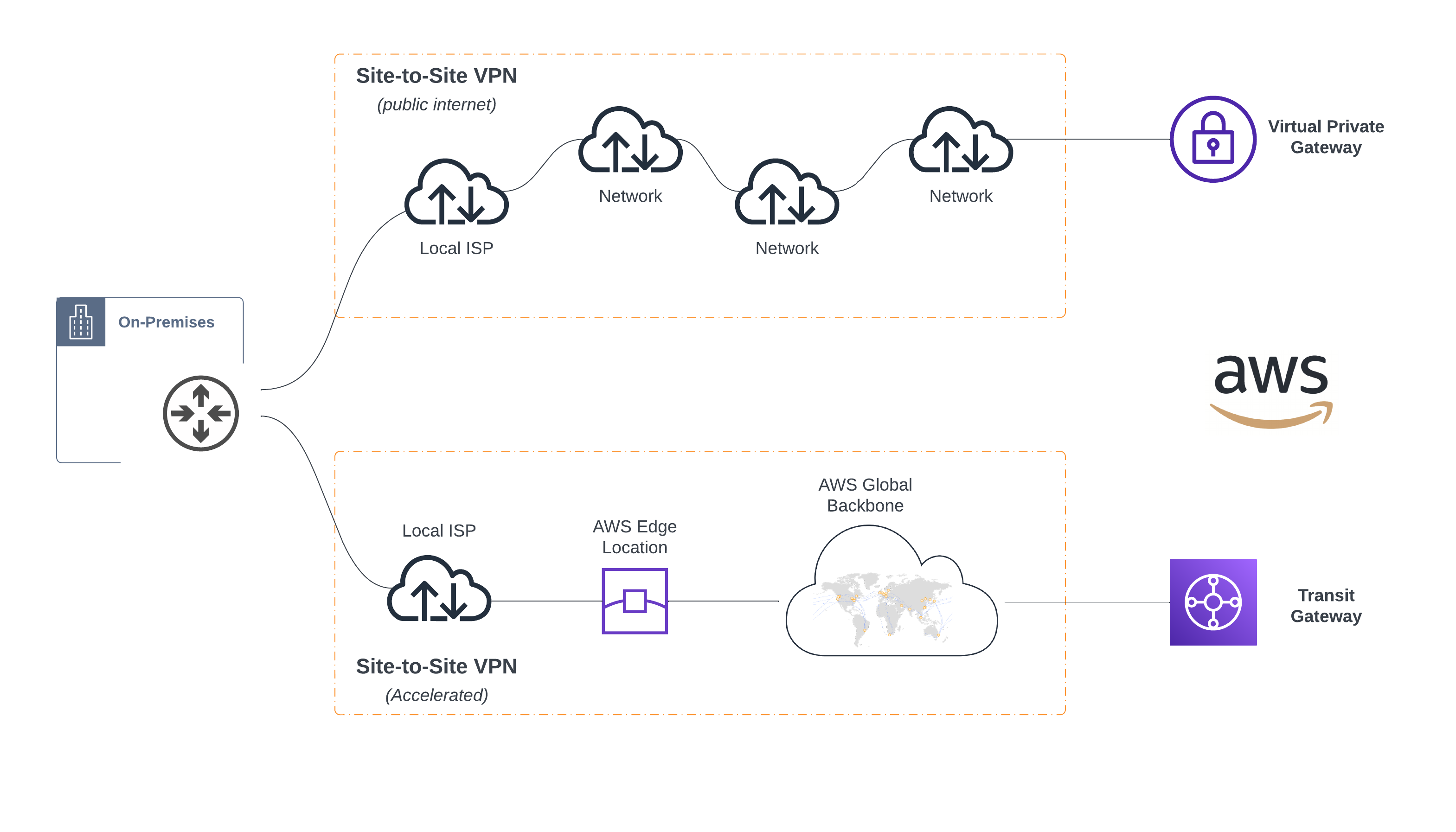
First things first, let’s define what AWS IoT VPN is all about. At its core, AWS IoT VPN is a service designed to establish secure connections between IoT devices and AWS services. It’s like creating a private tunnel where your data can flow freely without the risk of interception or tampering. This is crucial in an era where cyber threats are more sophisticated than ever.
Here’s why AWS IoT VPN is a big deal:
- It provides end-to-end encryption, ensuring your data remains confidential.
- It supports scalable communication, meaning it can handle everything from a handful of devices to thousands.
- It integrates seamlessly with other AWS services, giving you a unified platform for managing your IoT infrastructure.
In practical terms, AWS IoT VPN is like having a personal bodyguard for your IoT devices. It ensures that every bit of data transmitted between your devices and the cloud is protected. This is especially important for industries like healthcare, finance, and manufacturing, where data security is paramount.
- Deep Hot Link The Ultimate Guide To Unlocking Hidden Connections
- Sabrina Carpenter Erome A Rising Star Shining Brighter Than Ever
How AWS IoT VPN Works: A Step-by-Step Breakdown
Now that we know what AWS IoT VPN is, let’s talk about how it works. Understanding the mechanics can help you appreciate its power and versatility. Here’s a simplified step-by-step process:
1. Device Registration: First, you need to register your IoT devices with AWS. This involves assigning unique identities to each device, ensuring they can be authenticated.
2. Secure Connection: Once registered, devices can establish a secure connection to AWS using the IoT VPN. This connection is encrypted, making it nearly impossible for unauthorized parties to intercept data.
3. Data Exchange: With the secure connection in place, devices can exchange data with AWS services. This could include sending sensor readings, receiving commands, or updating firmware.
4. Monitoring and Management: AWS provides tools to monitor and manage your IoT devices in real-time. You can track performance, troubleshoot issues, and apply updates as needed.
Think of it like a well-oiled machine. Each step is designed to ensure smooth, secure, and efficient communication between devices and the cloud. It’s this level of precision that makes AWS IoT VPN a standout solution in the IoT space.
Key Features of AWS IoT VPN
So, what makes AWS IoT VPN so special? Let’s take a closer look at its key features:
End-to-End Encryption
Encryption is the backbone of AWS IoT VPN. It ensures that all data transmitted between devices and the cloud is scrambled, making it unreadable to anyone who intercepts it. This level of security is essential for protecting sensitive information.
Scalable Connectivity
No matter how many devices you’re managing, AWS IoT VPN can handle it. Whether you’re dealing with a dozen smart home gadgets or an entire factory floor of industrial sensors, the service scales effortlessly to meet your needs.
Seamless Integration
AWS IoT VPN works seamlessly with other AWS services, such as AWS Lambda, S3, and DynamoDB. This integration allows you to build complex IoT solutions without worrying about compatibility issues.
These features, among others, make AWS IoT VPN a robust choice for anyone looking to enhance their IoT infrastructure. But don’t just take our word for it—let’s look at some real-world applications.
Real-World Applications of AWS IoT VPN
So, where is AWS IoT VPN being used in the real world? Here are a few examples:
- Smart Cities: IoT devices are being deployed to monitor traffic, air quality, and energy usage. AWS IoT VPN ensures these devices can communicate securely with cloud services for data analysis and decision-making.
- Healthcare: Wearable devices and medical sensors rely on secure connections to transmit patient data. AWS IoT VPN provides the encryption and authentication needed to protect sensitive health information.
- Manufacturing: Industrial IoT devices are used to monitor equipment performance and optimize production processes. AWS IoT VPN ensures these devices can communicate reliably with cloud-based analytics platforms.
These applications highlight the versatility and power of AWS IoT VPN. It’s not just a tool for tech enthusiasts—it’s a solution that’s making a real impact across industries.
Setting Up AWS IoT VPN: A Beginner’s Guide
If you’re ready to dive in, setting up AWS IoT VPN is easier than you might think. Here’s a quick guide to get you started:
Step 1: Create an AWS Account
First, you’ll need an AWS account. If you don’t already have one, sign up at the AWS website. It’s free to start, and you can explore many services without incurring costs.
Step 2: Set Up IoT Core
AWS IoT Core is the foundation for managing your IoT devices. Use the AWS Management Console to create a new IoT Core instance and configure your settings.
Step 3: Register Your Devices
Next, register your IoT devices with AWS. Assign unique identities and certificates to each device to ensure secure authentication.
Step 4: Establish a Secure Connection
Finally, establish a secure connection using AWS IoT VPN. Follow the documentation to configure your devices and test the connection.
With these steps, you’ll have AWS IoT VPN up and running in no time. Of course, there’s more to explore, but this should give you a solid starting point.
Troubleshooting Common Issues
Even the best technologies can encounter hiccups. Here are some common issues you might face with AWS IoT VPN and how to fix them:
- Connection Problems: Ensure your devices are properly registered and that certificates are correctly configured.
- Data Transfer Delays: Check your network settings and ensure there are no bottlenecks affecting performance.
- Authentication Failures: Verify that device identities and certificates are valid and up-to-date.
By addressing these issues proactively, you can maintain a smooth and reliable IoT ecosystem.
Security Best Practices for AWS IoT VPN
While AWS IoT VPN provides robust security features, there are additional steps you can take to enhance protection:
- Regularly Update Certificates: Keep your device certificates current to prevent unauthorized access.
- Monitor Activity: Use AWS CloudWatch to track device activity and detect any suspicious behavior.
- Limit Permissions: Grant devices only the permissions they need to function, reducing the risk of misuse.
By following these best practices, you can ensure your AWS IoT VPN setup remains secure and reliable.
Future Trends in AWS IoT VPN
As technology continues to evolve, what’s on the horizon for AWS IoT VPN? Here are a few trends to watch:
Enhanced Machine Learning
AWS is investing heavily in machine learning to improve IoT capabilities. Expect to see more intelligent features that optimize device performance and security.
Edge Computing Integration
Edge computing is becoming increasingly important for IoT applications. AWS IoT VPN is likely to integrate more closely with edge devices, reducing latency and improving efficiency.
Global Expansion
As AWS expands its global infrastructure, expect AWS IoT VPN to become even more accessible and reliable for users worldwide.
These trends point to a bright future for AWS IoT VPN, one where it continues to push the boundaries of what’s possible in the IoT space.
Conclusion: Why AWS IoT VPN Matters
Wrapping up, AWS IoT VPN is more than just a tool—it’s a cornerstone of modern IoT infrastructure. From its robust security features to its seamless integration with other AWS services, it offers a comprehensive solution for managing IoT devices.
So, what’s next? If you haven’t already, give AWS IoT VPN a try. Whether you’re building a smart home, optimizing industrial processes, or exploring new IoT applications, this service can help you achieve your goals. And don’t forget to share your experiences and insights in the comments below. Let’s keep the conversation going!
Table of Contents
- What Is AWS IoT VPN and Why Should You Care?
- How AWS IoT VPN Works: A Step-by-Step Breakdown
- Key Features of AWS IoT VPN
- Real-World Applications of AWS IoT VPN
- Setting Up AWS IoT VPN: A Beginner’s Guide
- Troubleshooting Common Issues
- Security Best Practices for AWS IoT VPN
- Future Trends in AWS IoT VPN
- Conclusion: Why AWS IoT VPN Matters


Detail Author:
- Name : Lafayette Rau
- Username : alexis.emmerich
- Email : elton13@abbott.com
- Birthdate : 1977-02-18
- Address : 8446 Watsica Forest Apt. 100 Port Rodrigo, MA 38768
- Phone : 415.290.0078
- Company : Casper, Wyman and Gutmann
- Job : Punching Machine Setters
- Bio : Ea accusamus ipsum ut est. Sunt commodi ipsa vel laborum. Fuga itaque voluptatem distinctio dolor adipisci enim. Minima ut pariatur sequi reiciendis quia. Illo illo et optio.
Socials
linkedin:
- url : https://linkedin.com/in/stephanie_xx
- username : stephanie_xx
- bio : Adipisci tenetur consequatur reiciendis.
- followers : 4259
- following : 2388
facebook:
- url : https://facebook.com/stephanie.kirlin
- username : stephanie.kirlin
- bio : Eveniet eveniet vel iure et tempore. Aut enim eligendi enim omnis quia qui.
- followers : 555
- following : 1776
twitter:
- url : https://twitter.com/stephaniekirlin
- username : stephaniekirlin
- bio : Quo ut commodi iusto consequatur. Voluptate iure amet eum tempora perferendis laboriosam libero et. Ea in sed temporibus rem nisi et nemo.
- followers : 6761
- following : 2400
tiktok:
- url : https://tiktok.com/@stephanie.kirlin
- username : stephanie.kirlin
- bio : Aspernatur atque et aut labore nesciunt est tempore.
- followers : 967
- following : 1628