AWS IoT Secure Tunnel: The Ultimate Guide To Connecting Devices Safely
So here's the deal, if you're diving into the world of IoT (Internet of Things) and looking for a way to securely connect devices without exposing them to the public internet, AWS IoT Secure Tunnel might just be your golden ticket. Imagine this—you’ve got devices spread across the globe, and you need to access them remotely, but the thought of opening up ports or setting up complex networks makes you sweat. Well, AWS has got you covered with this secure tunneling solution. Let’s jump in and see how this works.
Now, before we get too deep into the nitty-gritty, let me break it down for you. AWS IoT Secure Tunnel allows you to create secure, encrypted connections between devices and remote applications, all without exposing your devices to the public internet. This is a game-changer for businesses that need to manage IoT devices remotely but don't want to compromise on security. It’s like having a private hotline for your devices, keeping the bad guys out while letting you in.
In this guide, we’re going to explore everything you need to know about AWS IoT Secure Tunnel. From the basics to advanced use cases, we’ll cover it all. So, whether you're just starting out or you're already knee-deep in IoT, this article is going to be your go-to resource. Let’s get started!
- Movierulz Your Ultimate Guide To Streaming Movies Online
- Discovering Lara Rose Onlyfans A Comprehensive Guide
Table of Contents
- What is AWS IoT Secure Tunnel?
- How Does It Work?
- Why Use AWS IoT Secure Tunnel?
- Benefits of AWS IoT Secure Tunnel
- Setting Up AWS IoT Secure Tunnel
- Use Cases
- Security Features
- Cost Considerations
- Troubleshooting
- Conclusion
What is AWS IoT Secure Tunnel?
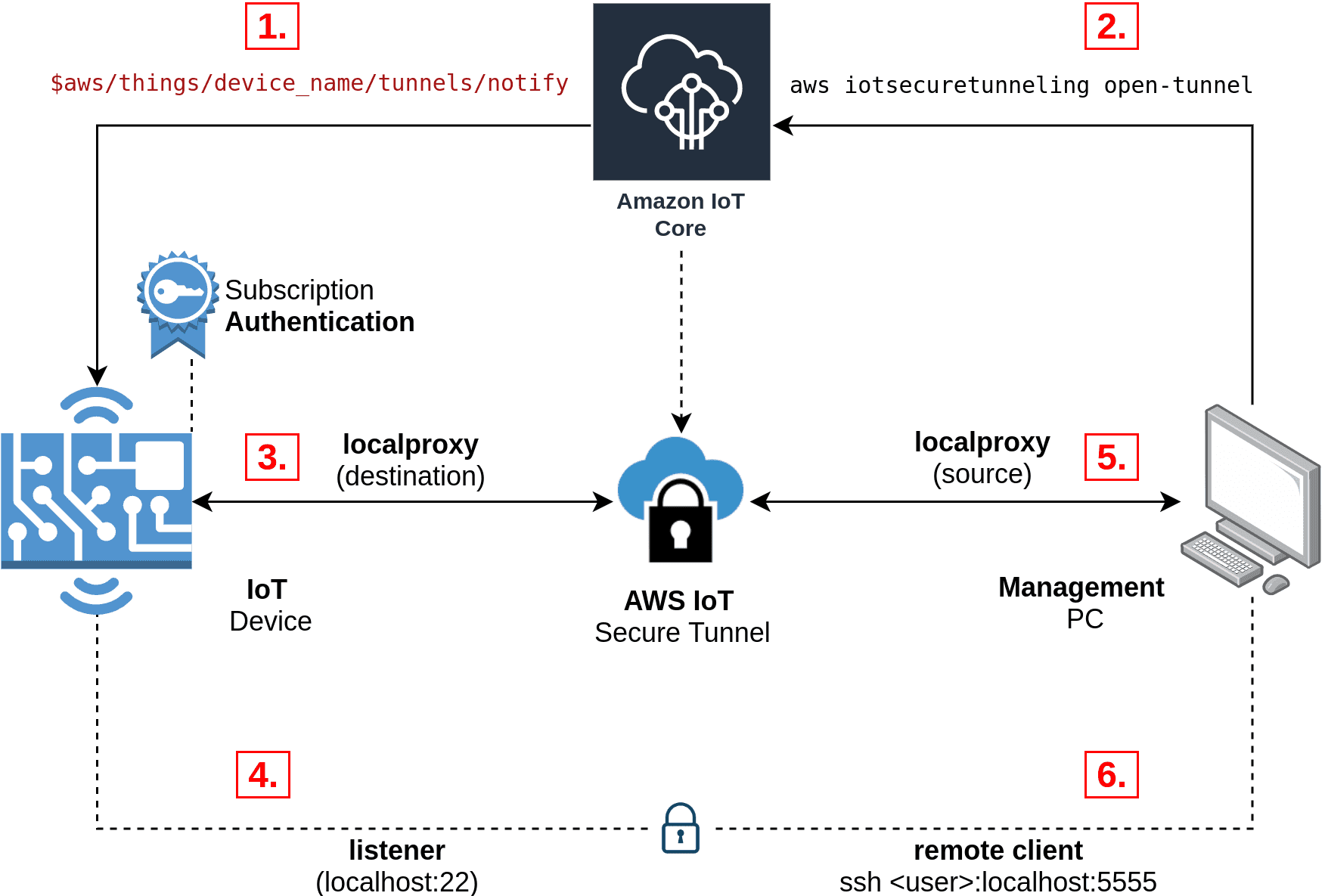
Alright, let’s start with the basics. AWS IoT Secure Tunnel is a service provided by Amazon Web Services that enables secure communication between IoT devices and remote applications. Think of it as a secure bridge that lets you access your devices without exposing them to potential threats on the public internet. This service is particularly useful for devices that are located behind firewalls or NATs, where traditional remote access methods might not work.
Here’s the kicker—AWS IoT Secure Tunnel uses end-to-end encryption, ensuring that your data stays safe during transmission. Plus, it doesn’t require you to open up firewall ports or set up complex network configurations. It’s like having a private network without all the hassle.
Why Secure Tunneling Matters
Secure tunneling is crucial in today’s interconnected world. With more and more devices being connected to the internet, the risk of cyberattacks increases exponentially. By using AWS IoT Secure Tunnel, you can mitigate these risks while still maintaining the flexibility to manage your devices remotely. It’s a win-win situation.
- Mkvmoviespoint X Your Ultimate Guide To Movie Downloads And Streaming
- Odisha Viral Mms Video The Untold Story Behind The Headlines
How Does It Work?
Let’s dive a little deeper into how AWS IoT Secure Tunnel actually works. The service uses a client-server architecture, where the device acts as the client and the remote application acts as the server. Here’s a quick breakdown:
- Device Registration: First, you register your device with AWS IoT. This involves setting up the necessary credentials and permissions.
- Tunnel Creation: Once the device is registered, you can create a secure tunnel using the AWS IoT Secure Tunneling API. This tunnel establishes a secure connection between the device and the remote application.
- Data Transmission: With the tunnel established, data can be transmitted securely between the device and the remote application. This data is encrypted using industry-standard protocols, ensuring maximum security.
It’s a pretty straightforward process, but the beauty lies in the details. AWS handles all the heavy lifting, so you don’t have to worry about the complexities of secure communication.
Key Components
Here are some of the key components involved in AWS IoT Secure Tunnel:
- AWS IoT Core: The backbone of the service, AWS IoT Core manages the communication between devices and the cloud.
- AWS IoT Device SDK: This SDK provides the necessary tools for device registration and tunnel creation.
- Remote Application: The application that connects to the device via the secure tunnel.
Why Use AWS IoT Secure Tunnel?
There are plenty of reasons why you should consider using AWS IoT Secure Tunnel. Let’s take a look at some of the most compelling ones:
First off, it’s all about security. By using AWS IoT Secure Tunnel, you can ensure that your devices remain secure while still being accessible remotely. This is especially important in industries where security is paramount, such as healthcare or finance.
Secondly, it simplifies the process of remote device management. Gone are the days of having to set up complex networks or deal with firewall configurations. AWS IoT Secure Tunnel takes care of all that for you, saving you time and effort.
Real-World Applications
Let’s talk about some real-world applications where AWS IoT Secure Tunnel shines. Imagine a scenario where you have a fleet of industrial machines located in different parts of the world. With AWS IoT Secure Tunnel, you can monitor and manage these machines remotely, without having to worry about exposing them to potential threats.
Another example is in the healthcare industry, where medical devices need to be monitored and maintained remotely. AWS IoT Secure Tunnel provides a secure way to access these devices, ensuring patient safety and data privacy.
Benefits of AWS IoT Secure Tunnel
Now, let’s talk benefits. There are several advantages to using AWS IoT Secure Tunnel, and here are some of the most significant ones:
- Enhanced Security: End-to-end encryption ensures that your data remains secure during transmission.
- Easy Setup: No need to configure firewalls or open ports—AWS IoT Secure Tunnel handles all that for you.
- Scalability: Whether you have a few devices or thousands, AWS IoT Secure Tunnel can scale to meet your needs.
- Cost-Effective: You only pay for what you use, making it a cost-effective solution for businesses of all sizes.
These benefits make AWS IoT Secure Tunnel an attractive option for anyone looking to securely connect IoT devices.
Comparing AWS IoT Secure Tunnel to Other Solutions
When it comes to secure tunneling solutions, AWS IoT Secure Tunnel stands out for its ease of use and robust security features. Compared to other solutions that require complex configurations and setup, AWS IoT Secure Tunnel offers a simpler, more streamlined approach.
Setting Up AWS IoT Secure Tunnel
Setting up AWS IoT Secure Tunnel is a relatively straightforward process. Here’s a step-by-step guide to help you get started:
- Create an AWS Account: If you don’t already have one, sign up for an AWS account.
- Set Up AWS IoT Core: Configure AWS IoT Core to manage your devices.
- Register Your Device: Use the AWS IoT Device SDK to register your device.
- Create a Secure Tunnel: Use the AWS IoT Secure Tunneling API to create a secure tunnel.
- Connect Your Application: Connect your remote application to the device via the secure tunnel.
That’s it! You’re now ready to start securely connecting your IoT devices.
Tips for Successful Setup
Here are a few tips to ensure a successful setup:
- Use Strong Credentials: Make sure to use strong credentials when registering your devices.
- Test Your Setup: Before deploying to production, test your setup thoroughly to ensure everything works as expected.
- Monitor Performance: Keep an eye on the performance of your secure tunnels to ensure they’re functioning optimally.
Use Cases
Let’s explore some of the most common use cases for AWS IoT Secure Tunnel:
- Remote Device Management: Manage IoT devices remotely without exposing them to the public internet.
- Industrial IoT: Monitor and maintain industrial machines located in different parts of the world.
- Healthcare: Securely access medical devices for remote monitoring and maintenance.
- Smart Homes: Control smart home devices securely from anywhere in the world.
These use cases demonstrate the versatility and power of AWS IoT Secure Tunnel.
Industry-Specific Use Cases
Here are some industry-specific use cases:
- Manufacturing: Use AWS IoT Secure Tunnel to monitor production lines and equipment in real-time.
- Utilities: Securely manage utility infrastructure, such as smart meters and substations.
- Agriculture: Monitor and control agricultural equipment remotely, optimizing crop yields.
Security Features
Security is at the heart of AWS IoT Secure Tunnel. Here are some of the key security features:
- End-to-End Encryption: All data transmitted through the secure tunnel is encrypted using industry-standard protocols.
- Identity Management: AWS IoT Core provides robust identity management features to ensure only authorized devices and applications can access the secure tunnel.
- Access Control: Fine-grained access control allows you to specify exactly who can access your devices.
These features make AWS IoT Secure Tunnel one of the most secure solutions available for IoT device management.
Best Practices for Security
Here are some best practices to enhance the security of your AWS IoT Secure Tunnel setup:
- Regularly Update Credentials: Keep your device credentials up to date to prevent unauthorized access.
- Monitor Logs: Regularly review logs to detect any suspicious activity.
- Implement Multi-Factor Authentication: Add an extra layer of security by implementing multi-factor authentication for your devices.
Cost Considerations
When it comes to cost, AWS IoT Secure Tunnel offers a pay-as-you-go pricing model. You only pay for the tunnels you create and the data you transmit. This makes it a cost-effective solution for businesses of all sizes.
Additionally, AWS offers a free tier for AWS IoT Secure Tunnel, allowing you to try out the service without any upfront costs. This is a great way to get familiar with the service before committing to a larger deployment.
Estimating Costs
Here’s how you can estimate your costs:
- Tunnel Creation: You’re charged per tunnel created.
- Data Transmission: You’re charged based on the amount of data transmitted through the tunnels.
By understanding these cost factors, you can better plan your budget for AWS IoT Secure Tunnel.
Troubleshooting
Even with the best-laid plans, issues can arise. Here are some common troubleshooting tips for AWS IoT Secure Tunnel:
- Check Device Registration: Ensure your devices are properly registered with AWS IoT.
- Verify Credentials: Double-check your device credentials to ensure they’re correct.
- Review Logs: Use AWS CloudWatch Logs to identify any issues with your secure tunnels.
By following these tips, you can quickly resolve any issues that may arise.
Getting Help
If you’re stuck, AWS provides excellent support resources, including documentation, forums, and support tickets. Don’t hesitate to reach out if you need assistance.
Conclusion
In conclusion, AWS IoT Secure Tunnel is a powerful tool for securely connecting


Detail Author:
- Name : Marcellus Dickinson
- Username : ebatz
- Email : brandy67@pagac.com
- Birthdate : 1977-03-31
- Address : 360 Corwin Rue Apt. 444 East Isaiah, RI 77084-1504
- Phone : +1-812-692-5534
- Company : Runte-Aufderhar
- Job : General Practitioner
- Bio : Qui cum repudiandae et harum. Dicta omnis est occaecati aut sint ut. Necessitatibus sint velit velit vel magnam est omnis doloribus. Ut quidem ad culpa nostrum.
Socials
tiktok:
- url : https://tiktok.com/@halvorsonc
- username : halvorsonc
- bio : Voluptates quis ducimus doloribus.
- followers : 1594
- following : 2621
twitter:
- url : https://twitter.com/halvorsonc
- username : halvorsonc
- bio : Quod laborum enim accusantium ullam eaque error repudiandae officia. Non dolores pariatur iste et nam in veniam. Nisi beatae ut quibusdam nesciunt laborum non.
- followers : 628
- following : 2085
linkedin:
- url : https://linkedin.com/in/cory_real
- username : cory_real
- bio : Aut at et delectus et ipsam.
- followers : 2946
- following : 2197